The contract lock is the first to access national network identity authentication and continues to provide legal and compliant electronic signature services
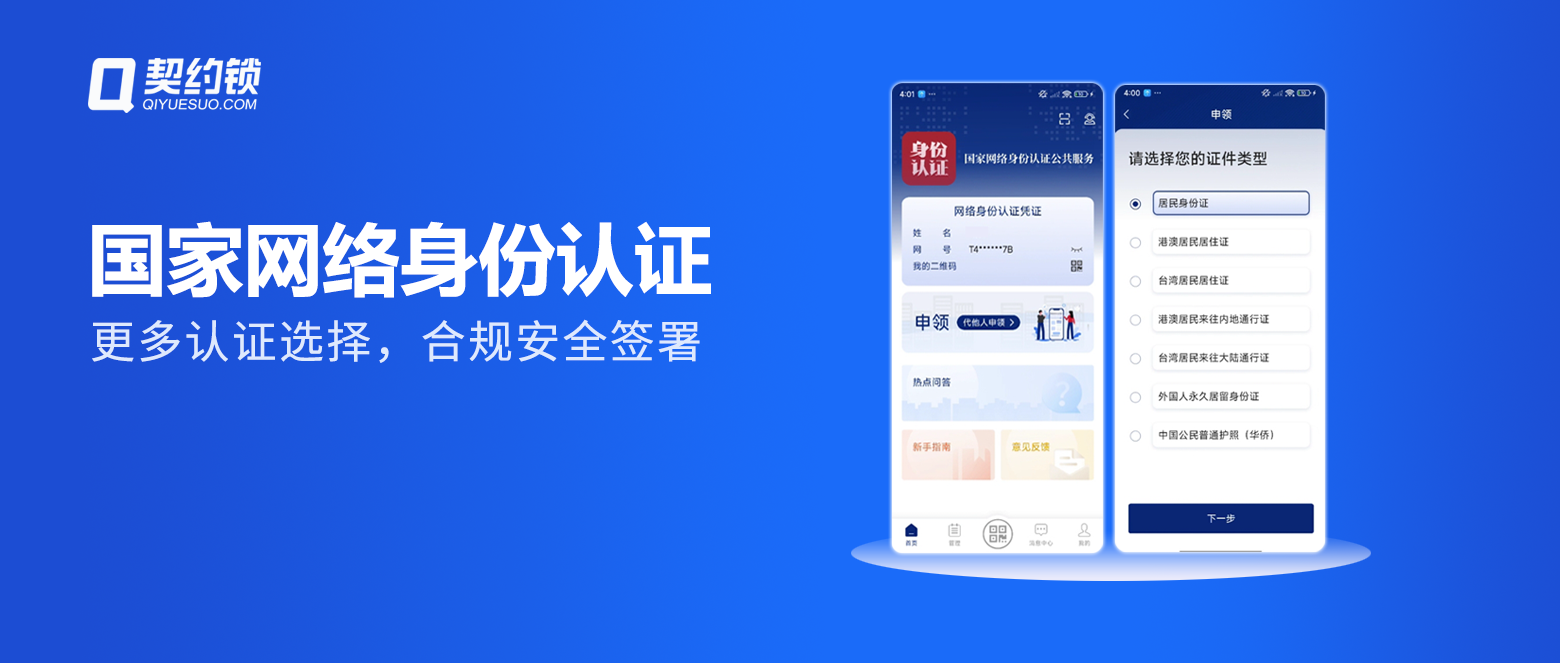
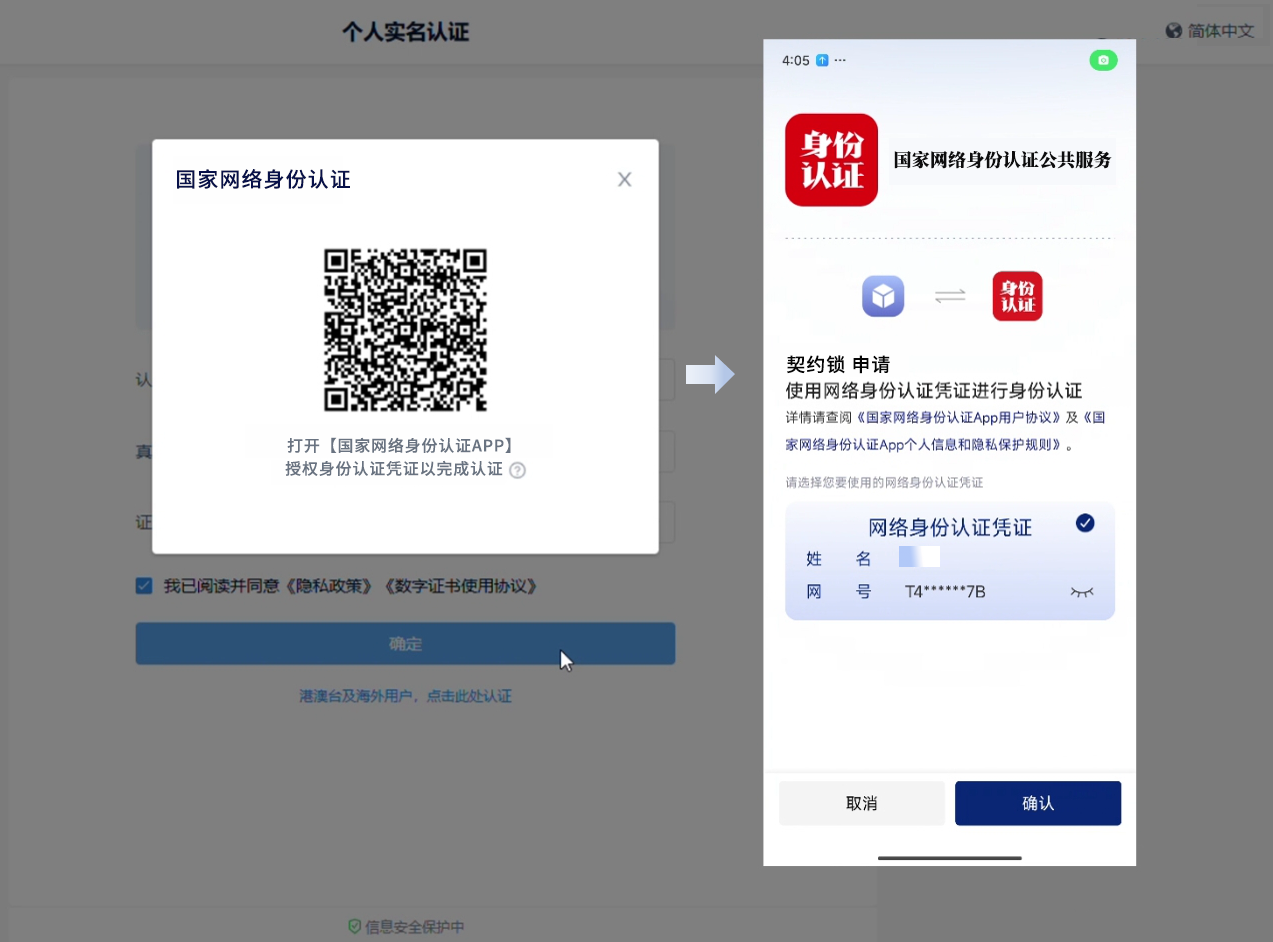
Recently, the contract lock intelligent electronic contract platform has been integrated; National Network Identity Authentication Public Service; Platform users can directly call the national network identity authentication results to complete real name authentication. Accelerate the popularization and application of national network identity authentication in electronic signature services, promote the achievement of the strategic goal of trusted network identity, and assist in the digital transformation of thousands of industries. The National Network Identity Authentication Public Service Platform is jointly organized and constructed by the Ministry of Public Security and multiple ministries. It relies on legal identity card information and the national population database to provide secure and authoritative network identity authentication services to the entire society. Individual users who sign electronic contracts on the Contract Lock platform through service docking can directly download them; National Network Identity Authentication App; Real name authentication can be quickly completed by simply scanning the code for authorization during the identity verification process. Avoid collecting too much user information and protect user information security. (Scan code to quickly complete national network identity authentication credential authorization) span data style apply id="font-size-71e076dd" styl
E="font size: 16px;">In response to the national call, promote the trustworthiness of online identities
2024 Since, the Ministry of Public Security and the National Internet Information Office have issued intensive policies to strengthen the requirements of online identity authentication and implement the national strategy of online trusted identity:
· On July 26, 2024, a joint release was made of the "National Network Identity Authentication Public Service Management Measures (Draft for Comments)", which aims to launch a pilot program for national network identity authentication public services and provide unified issuance for the general public; Network Number” “ Online Certificate” Provide real identity registration and verification services based on legal identity document information.
· On March 13, 2025, a joint release of the "Measures for the Security Management of Facial Recognition Technology Applications" was issued, which clearly stipulate in Article 11 that "; For the application of facial recognition technology to verify personal identity and identify specific individuals, priority is encouraged to use channels such as the National Population Basic Information Database and the National Network Identity Authentication Public Service to reduce the collection and storage of facial information and protect facial information security;.
AsElectronic SignatureAs a leading service provider in the industry, Contract Lock is the first to integrate into the national network identity authentication public service.Providing users with more compliance authentication methods to choose from, it continues to provide convenient trusted identity support for cross provincial government services, as well as for the full process network operation of finance, leasing, procurement, sales and other businesses, accelerating the construction of a trusted foundation in the digital age..
Compliance certification services, building a trusted foundation for digitalization
《 The Electronic Signature Law clearly stipulates that reliable electronic signatures must meet the following requirements:; The signatory's identity is genuine, the signing intention is clear, and the data cannot be tampered with; Three major conditions, compliant and secure identity authentication is an important component of the validity of electronic contracts.
As a professional provider of electronic contract products, Contract Lock has obtained numerous qualification certificates such as ISO27001 Information Security Management System Certification. It integrates various authoritative authentication methods such as CA certification and national network identity authentication to provide users with trustworthy identity authentication services that comply with legal and regulatory requirements, and build a trustworthy digital foundation for business:
· Authoritative authentication integration:Cooperate with the National Network Identity Authentication Public Service Platform and CA institutions across the country that have been authorized by the Ministry of Industry and Information Technology and issued electronic authentication licenses to provide identity authentication and electronic signing services for users, ensuring the authenticity, trustworthiness, and non repudiation of user identities in digital scenarios such as electronic signing.
· Multiple authentication options available:Supports various authentication methods such as facial recognition, voice and video recording, SMS verification, UKey verification, etc., to meet the security level requirements of different scenarios. For example, high-sensitivity operations (such as signing large contracts) require the addition of biometric and dynamic interfaces to ensure operational safety.
· Zero intervention principle: The authentication process is independently completed by the user, and the contract lock platform focuses on providing electronic signature services, only providing technical interfaces and certification services, and does not determine or intervene in the authentication results, ensuring that the authentication procedures in electronic signature activities comply with the requirements of the Electronic Authentication Service Management Law, the process is compliant, and the results are trustworthy.
· Full chain certification:Integrating blockchain certification, notary office certification and other services to help preserve the complete record of the certification process, ensuring traceability of the certification process and the credibility of the certification results by the court.
Meet the identity authentication requirements in various business scenarios
Identity authentication is widely used in digital scenarios such as electronic signing and online office work. Contract locks, with their powerful integration capabilities, provide identity authentication services for various management software, APP applications, mini programs, etc.Intelligent verification of the operator's true identity in system login, process approval, signature and seal, data viewing, information release, file download, message communication, file borrowingand other links to ensure personal operation.
At present, contract locking is deeply applied in various business scenarios such as government services, contract signing, bank account opening, insurance sales, hospital electronic prescription issuance, university seals, testing report issuance, as well as engineering material procurement, bidding, etc. It can provide identity authentication solutions according to customers' specific business scenarios at any time, allowing business digitization to provide trusted support:
· Contract signing: In the signing scenarios of labor contracts, sales contracts, etc., the identity of the signatory is verified through facial recognition, national network identity authentication, and other methods to prevent proxy signing and ensure the effectiveness of the signing.
· Bank account opening and loan: In the process of bank account opening and loan approval, combined with CA institution digital certificates and national certification results, a dual trust chain is built to simplify the manual identity review workload of banks and assist in business compliance and security.
· Supplier authentication:Suppliers can complete identity authentication without on-site presence, and support the activation of supplier business information inspection to automatically monitor changes, ensuring identity transparency, change visibility, and secure signing.
· Government service processing:Docking with the government system to meet the online authentication needs of users' real identities in services such as public finance data query, online signing and filing of housing, and real estate registration, promoting the implementation of online and cross provincial government service processing.
· Insurance sales: In the reimbursement sales process, direct users register and purchase insurance products with real names, and the signing process synchronously verifies the real identity information of both consumers and insurance institutions, packaging the rights and interests of both parties, and promoting compliant online insurance sales.
· Electronic medical record issuance:Establish a trusted identity system covering all medical staff in the hospital, realize online identity verification for medical staff, and create and use authorized electronic signatures to ensure the credibility of the signing process and results of various documents such as electronic prescriptions, medical orders, nursing orders, etc.
· Expense reimbursement approval:For large amount of internal fund reimbursement business of central state-owned enterprises, identity authentication and verification services can be intelligently integrated in the approval process to ensure compliance approval by responsible persons and ensure fund security.
…
Summary
“ Clarify the true identity and true intention of the operator; Contract lock has become one of the fundamental requirements for every organization in the digital age, and we focus on doing it well< span data-style-apply-id="font-family-62ebe55b" style="font-family: Arial,Helvetica,sans-serif;">
Frequently Asked Questions and Answers (FAQ) about Electronic Contract Identity Authentication
Q: If the contact information of the authenticated user has changed, does it need to be re authenticated?
A: need. To ensure the validity of the contract, the contract lock platform will automatically detect the validity period of the documents and synchronously adjust the authentication status of users whose information has changed to“ Unverified” We need to resend the authentication notification and authenticate.
Q: If the name on the contract is signed incorrectly, does it have legal effect?
A: The appearance of a signature is not related to the legal validity of an electronic signature. The basis for determining the validity of electronic signatures is the digital certificate behind the appearance of the signature, which contains the real identity information of the actual signatory's real name authentication.
So, no matter what name you sign, even if it's not yours, the digital certificate attached to the signature is yours, and you can prove that the signatory is you by verifying the digital certificate. Of course, to avoid unnecessary trouble in the future, you can unlock it through a contract lock before signing; Note verification;.
Q: How to ensure that the identity authentication process is not impersonated or tampered with?
A: The contract lock platform collaborates with authoritative databases to compare user identity information in real-time, and uses technologies such as liveness detection, timestamps, and blockchain authentication to prevent forgery. At the same time, the key data is encrypted and transmitted throughout the entire process. Currently, the contract lock has obtained ISO27001 information security management system certification and other certificates to ensure compliance and security.
Q: Will my personal information be leaked after identity authentication?
A: Through legitimate platforms,“ The principle of least necessity; Collect only necessary information, store and transmit data encrypted, and anonymize sensitive information (such as displaying only the last four digits of the ID card). At the same time, the platform must comply with the Personal Information Protection Law and shall not provide data to third parties without user authorization.
Q: What is the difference between national network identity authentication and CA authentication?
A: The national network identity authentication integrates authoritative data from the national population database and provides authentication services for identity documents, focusing on verifying the true identity of individuals; CA authentication is based on a digital certificate trust system provided by a third-party authoritative organization, used to ensure data transmission security and identity trustworthiness. Both authentication results have legal effect, and the appropriate authentication method needs to be selected according to the business scenario in the contract lock.
Q: What are the differences between certificates issued by different CA institutions?
A: Due to the fact that CA institutions require licenses to be issued by the state and are official authoritative institutions, there is essentially no difference in the legal validity of certificates issued by different CA institutions. However, it is possible to selectively select a certain certificate based on the cooperation between the client and the CA institution.
 沪公网安备 31011202012092号
沪公网安备 31011202012092号